Security remains a paramount concern in the Decentralized Finance (DeFi) market sector. As these platforms gain popularity, offering unprecedented financial freedom and opportunities, they become attractive targets for cybercriminals.
The question of whether some of the top DeFi projects could be compromised is critical. It touches on vulnerabilities that range from smart contract flaws to governance weaknesses.
The One Thing Preventing DeFi Hacks
Ronghui Gu, co-founder of blockchain security firm Certik, provided BeInCrypto with invaluable insights into the complex DeFi market. According to him, the bedrock of securing DeFi platforms is thorough auditing.
“Auditing can help identify vulnerabilities by meticulously analyzing code to detect potential reentrancy issues or other exploitable flaws. This process involves rigorous testing against known attack vectors, fuzzing, thorough code review, and validation against best practices,” Gu told BeInCrypto.
Multichain’s exploit, resulting from centralized key control, exemplifies the dangers of such vulnerabilities. While audits might not change a project’s structural decisions, they highlight risks, offering a chance for mitigation.
According to Gu, effective audits should thoroughly assess the implementation of multi-signature wallets. He also pointed out the necessity for regular security training for team members handling private keys. This comprehensive approach to auditing, from code analysis to operational security practices, is vital in enhancing a platform’s resilience against attacks.
When addressing governance system vulnerabilities, as highlighted by the Tornado Cash governance exploit, Gu advocates for a comprehensive review of the governance process. This includes scrutinizing proposal creation rules, voting power distribution, and the execution conditions of proposals.
Such an audit identifies potential vulnerabilities and ensures checks and balances are in place to prevent disproportionate control by any single entity.
“Assessing the security implications of each step in the governance process should help verify that there are adequate checks and balances in place. This can prevent any single entity or group from exerting disproportionate control. Auditors must test critical parameters like quorum requirements, voting thresholds, and time lock durations to balance efficiency with security,” Gu added.
New Technologies for Regular Auditing
The technological advancements in auditing, as Gu mentioned, include integrating machine learning and developing specialized tools tailored to DeFi’s unique challenges. This approach enables rapid code analysis, uncovering vulnerabilities that could go unnoticed until exploited.
Machine learning’s ability to adapt and learn from past exploits promises a dynamic defense mechanism against new threats. Predictive modeling further enhances this capability, identifying potential vulnerabilities under various stress scenarios before they can be exploited.
“Dynamic analysis, which tests the smart contract in a live environment, is vital for uncovering runtime errors and more intricate vulnerabilities that only manifest during execution. Given the evolving nature of threats, continuous monitoring and regular re-auditing are crucial, particularly when updates or modifications are made to the contract,” Gu explained.
However, technology alone is not a panacea. Developing tools and frameworks specifically designed for DeFi’s unique challenges is crucial. These include the analysis of complex smart contract interactions and the simulation of economic attacks.
Collaboration within the DeFi community is another cornerstone of a robust security strategy. By sharing knowledge and resources, auditors can remain abreast of emerging threats and refine best practices for the industry’s collective benefit. Training and developing talent with a deep understanding of blockchain technology, and cybersecurity is also vital, ensuring teams are equipped to navigate the complexities of DeFi auditing.
“Developers, as the builders of this industry, should be up to date on the latest vulnerabilities and best practices. The open-source nature of crypto is one of its greatest strengths, and we should continue to prioritize that going forward. It means that one platform’s mistake doesn’t have to be repeated, everyone can learn from it,” Gu added.
The inherent complexity of DeFi projects introduces several common vulnerabilities, from smart contract flaws to governance mechanisms and the risk of composability. These vulnerabilities highlight the importance of comprehensive security reviews, which must delve into smart contract code, governance structures, and protocol integrations.
The frenetic pace of DeFi development, while driving innovation, often leads to compromises in security, increasing the risk of attacks.
Are All DeFi Platforms Compromised?
For users, navigating the DeFi sector requires diligence and an understanding of the inherent risks. Engaging with platforms demands a proactive approach, from researching a project’s security history to staying informed about the broader ecosystem.
Gu emphasized that transparency can help DeFi platforms foster trust and facilitate community learning. Therefore, this ensures that one platform’s mistake can be a lesson for others.
“An important factor is the project’s transparency regarding its governance structure and codebase. Open-source projects with clear and well-documented code are generally more trustworthy. The presence of a KYC (Know Your Customer) program for the project’s lead contributors is also a sign of a project’s commitment to integrity and transparency,” Gu said.
Tools like Certik’s Security Leaderboard and Skynet, as well as Beosin EagleEye, Hacken, Blowfish and SlowMist, provide valuable insights into a project’s security posture. According to Gu, these offer real-time monitoring and security rankings so users can make more informed decisions and minimize risk exposure, especially in a sector where nearly $5.80 billion has been hacked.
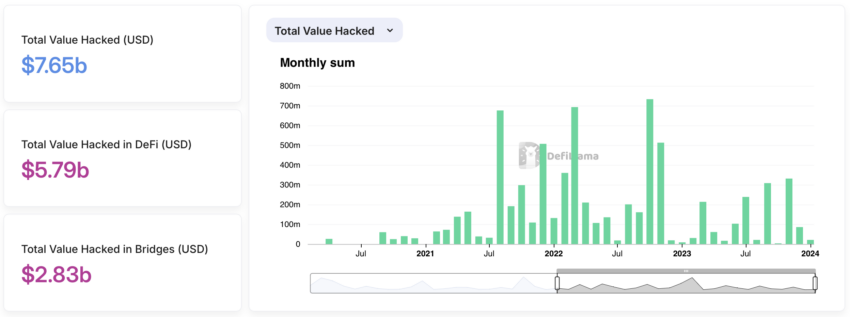
Total Value Hacked in Crypto. Source: DeFiLama
As DeFi continues to redefine the financial system, the emphasis on security cannot be overstated. Integrating advanced technologies, specialized tools, and community collaboration is pivotal in safeguarding the ecosystem. However, the responsibility also lies with users to exercise vigilance and with developers to prioritize security at every development stage.
Only through a concerted effort can the DeFi space mature into a secure, stable, and thriving environment for innovation.
Disclaimer
Following the Trust Project guidelines, this feature article presents opinions and perspectives from industry experts or individuals. BeInCrypto is dedicated to transparent reporting, but the views expressed in this article do not necessarily reflect those of BeInCrypto or its staff. Readers should verify information independently and consult with a professional before making decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.


